Low Level
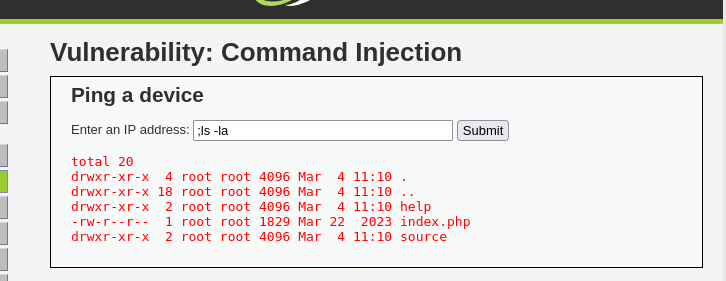
- Functionality Check: Application accepts input in
ipparameter, directly passed toshell_exec(). - Injection: Concatenated
;ls -laas payload. - Vulnerability: Lack of input validation allows command execution.
|
|
- The script serves as a Proof of Concept (PoC) to exploit a command injection vulnerability in a web application.
- It demonstrates how an attacker can execute arbitrary commands on the target system through the vulnerability.
- By injecting specially crafted commands, the attacker gains unauthorized access to the system.
- This unauthorized access can lead to further exploitation, such as data theft, system compromise, or launching other attacks.
- It’s crucial to emphasize that exploiting vulnerabilities without proper authorization is both illegal and unethical.
Medium Level
- Functionality Check: Application continues to execute OS commands.
- Input Validation: Concatenated
|as payload. - Bypass: Used
|ls -lapayload for successful execution.

High Level
- Functionality Check: Application still executes OS commands.
- Tightened Validation: Additional characters like
&, ``,$,(replaced with space. - Bypass: Identified space after
|character, used127.0.0.1|ls -lspayload for success.

